No one wants to be a victim of cybercrime, however, it happens every single day. Most cyber crimes go undetected for months, even years, in some cases. But knowing what to look for can help you from becoming part of the next news cycle.
 Below, we’ll give you a few signs to look for to see if your business has been a victim of cyber crime.
Below, we’ll give you a few signs to look for to see if your business has been a victim of cyber crime.
Ransomware Demands
You know the sinking feeling of despair you get when you see the blue screen of death?
Well, that’s nothing when compared to a ransomware demand screen.
Ransomware screens lock you out of your computer completely, generally with a demand to pay the hackers using “untraceable” currency such as Bitcoin and/or gift cards.
Most ransomware demands are legitimate, and will absolutely destroy your computer and all the files on the system.
Unfortunately, some of the best ransomware threats are unable to be stopped unless you cave into their payment requests.
Some ransomware variants have been nullified by antivirus companies, but a ransomware demand screen means you’ve been a victim of cyber crime.
At this point, you need to turn your computer completely off and run a security audit on the computer system.
Until the threat has been removed, there is no reason to continue using the compromised system.
Being Controlled By Someone Else
Do you leave your computer on when you leave work for the day?
A lot of employees do …
Have you ever come back to your computer and noticed that the screen doesn’t look the same as when you left?
Or maybe your mouse will move around on its own while you are actually on the computer?
Maybe you open a program, but notice another program open/close almost instantly?
There’s a good chance that your system and/or network has been compromised?
There are a lot of tools that hackers can use to control your computer remotely. They can watch what you are doing, record your keystrokes, and watch you using your camera.
If you think you’ve been compromised, then you need to run a security audit to make sure that any vulnerabilities that led to the compromise have been fixed.
Redirected Searches
Have you ever typed in eBay in Google or Bing and had some odd result page come up that looks nothing like you expected?
Or maybe the results look fine, but when you click on the link, it takes you to something else completely different?
There’s a good chance that your browser has been hijacked.
Hijacking is not easily detectable in most cases.
Most hackers have done a good job of masking their activities, but some hijacking threats just get worse over time.
In most cases, a hijacked browser is more a nuisance than a threat. But the fact that the browser has been hijacked means your system and/or network is compromised.
Once you’ve identified that your system and/or network has been compromised, you need to run a security audit to identify the vulnerabilities and the threat.
Until then, the compromised computer system and/or network should not be used by anyone in the company until the vulnerability has been patched and the threat has been removed.
Webpages Not Responding Properly
Another sign that your business has been the victim of cyber crime is the fact that web pages you’ve visited before aren’t working as they should.
For instance, maybe you’ve gone to the Bank of America website for your financial statements numerous times.
You type in your username and password, click on Login, and everything works great. But today, you click on Login and nothing happens.
So you try again …
And again …
You quit trying, thinking that their website is down or having problems.
You go back again later in the day, but the same thing is still happening.
There’s a good chance that your username and password have been captured.
Websites that don’t use 2FA can be susceptible to these types of attacks.
2FA, or two-factor authentication, uses more than just a username and password to gain entry into their website.
A 2FA enabled website will confirm your identity through SMS, Phone, Email, or some other secondary method that can verify that it’s you requesting access.
If your credentials were captured, the hacker still would not be able to gain access on a 2FA enabled website.
If you aren’t sure if a website supports 2FA, all you have to do is use this 2FA support verification tool.
We tested BankofAmerica.com to see if it supported 2FA. Here are the results:
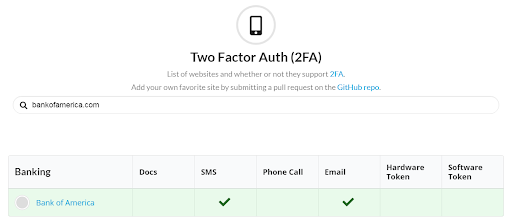 As you can see, BankofAmerica.com supports 2FA through SMS messaging and/or email.
As you can see, BankofAmerica.com supports 2FA through SMS messaging and/or email.
If a website stops working properly, there is a good chance that your computer system and/or network has been compromised.
If you suspect your computer system and/or network has been compromised, you should run a security audit to see what needs to be done to fix the vulnerability and remove the threat.
Ways To Prevent the Next Cyber Crime Event
A lot of companies install antivirus programs to monitor their computer systems.
While this is a good first step, it’s not enough in most cases.
Having a security professional in-house and/or on-call is the next best option. But, for most companies, the cost associated with this is too high.
That’s why most businesses work with cybersecurity vendors.
Because these vendors focus solely on cybersecurity, their level of expertise in the area of protecting companies against cybercriminals are unmatched.
Compared to hiring a single cybersecurity personnel, businesses are far more protected when they assign their network’s protection to a vendor that specializes in cybersecurity.
What’s more, these security companies are equipped with cybersecurity-related tools and methodologies.
One such methodology they use is infrastructure testing — a process where the cybersecurity company uses the procedures, strategies, and tools used by real-world hackers to uncover weak points in their client’s IT security.
By running an infrastructure test, companies are able to fortify the gaps in their IT security even before their network falls prey to cybercriminals.
Cybercrime isn’t slowing down.
 Our dependency on the internet, and being connected, puts us at risk more each day.
Our dependency on the internet, and being connected, puts us at risk more each day.
Plus, we just keep adding more IoT devices that aren’t nearly as secure as we would like to think.
If you have been the victim of cybercrime, you need to find the vulnerabilities and patch them up. Then remove the actual threat from your system.
If you don’t know what to do, or how to do it, then you need to contact a security provider to help resolve these issues before they compromise your company and/or your customers.